
Enable Comprehensive Data Visibility and Streamline Compliance
Most organizations lack visibility into where sensitive data resides. Hidden risks are everywhere. A user may have files with Social Security numbers in their downloads folder. SharePoint folders may contain credit card numbers, and file shares may store PII in images. PK Protect Endpoint Manager (PEM) discovers sensitive data and applies policy-driven protections. This reduces risk and ensures secure, compliant data use.
Why PK Protect Endpoint Manager
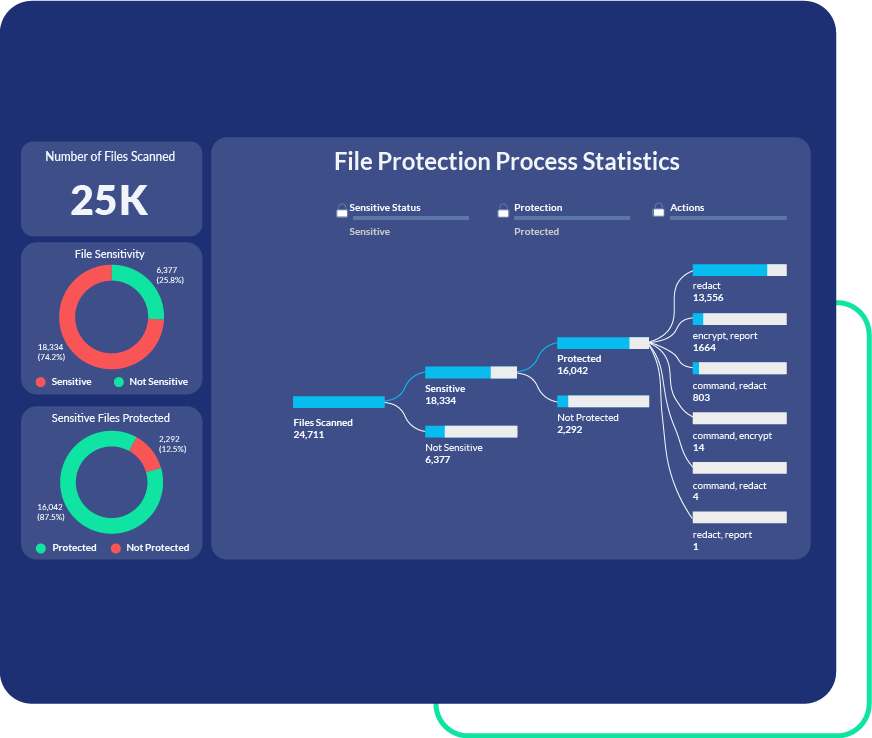
Centralized Data Security Without User Dependence
Our endpoint data protection suite centrally enforces protection policies. This allows you to label, encrypt, redact, move, delete, or quarantine sensitive data automatically without relying on user behavior. Unlike user-applied security, which introduces risk, PEM provides consistent, enterprise-wide protection and compliance that users can’t override.
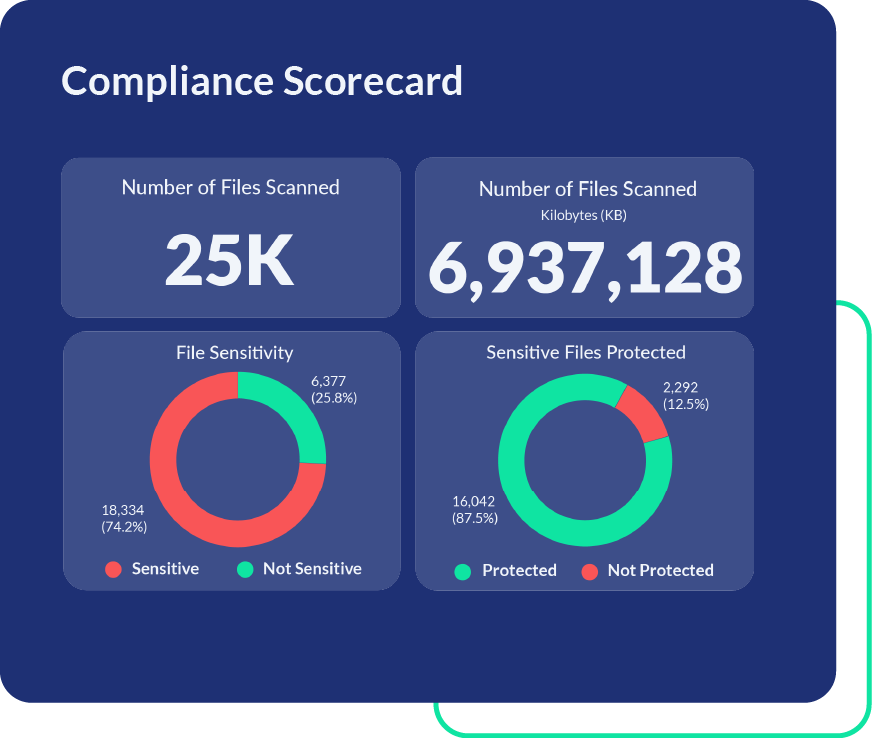
Persistent Protection That Preserves Productivity and Ensures Compliance
PEM’s data-centric security follows your data, at rest or in motion. This minimizes exposure and supports rapid compliance with regulations like PCI, GLBA, SOX, GDPR, and HIPAA. Ensure seamless access for authorized users while maintaining usability and eliminating risky workarounds.
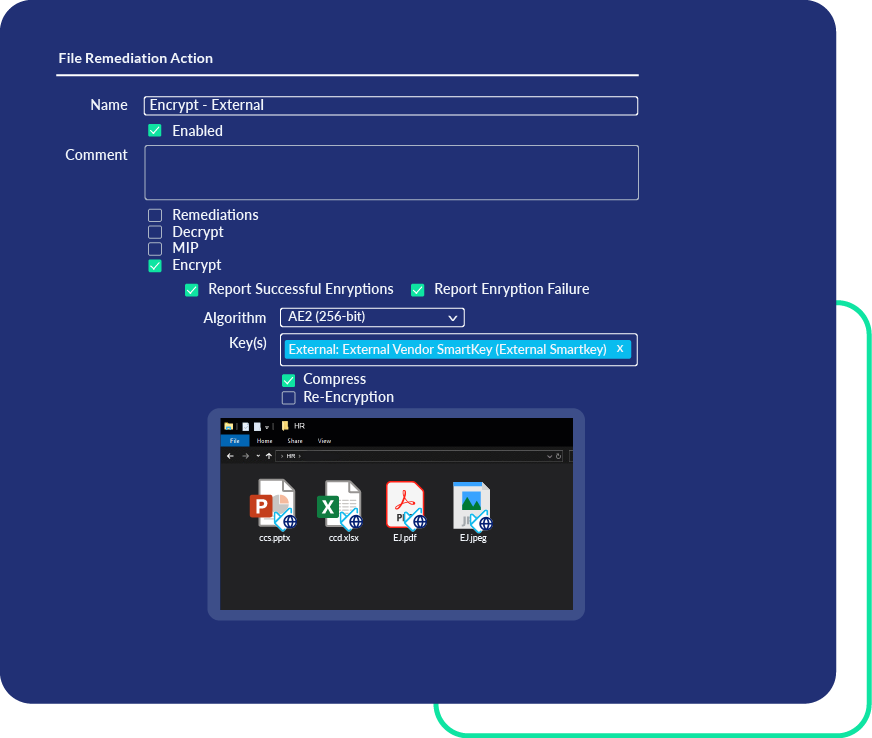
Beyond Purview: Enterprise-Wide Visibility and File-Level Protection
Microsoft Purview offers visibility within its own ecosystem. Our endpoint protection security suite expands this with visibility across your entire organization. It closes critical gaps with file-level encryption for all file types. Redaction also secures a wide range of formats, including CSVs and legacy or unsupported Microsoft files (e.g., .ppt,.doc, .xls). Purpose-built for data security and compliance, PEM includes customizable, pre-built policies that require minimal tuning and configuration.

Encryption at Enterprise Scale
FISERV, one of the world’s largest financial services providers, encrypts over one million files daily. This demonstrates PEM’s ease of use and ability to meet compliance requirements in complex environments. Our automation encrypts data at scale, which historically has been impractical, inefficient, and cost-prohibitive.







