End-to-End Data Discovery and Protection for M&A
In any M&A deal, you must audit and report on personal and sensitive data to reveal risks. Before you migrate, you need to identify where PII or IP exists and how you’ll ensure its security. PK Protect supports this with discovery and remediation.
We Keep You Compliant as You Evolve
Complete Data Security for M&A and Divestitures

Precise, Scalable Discovery
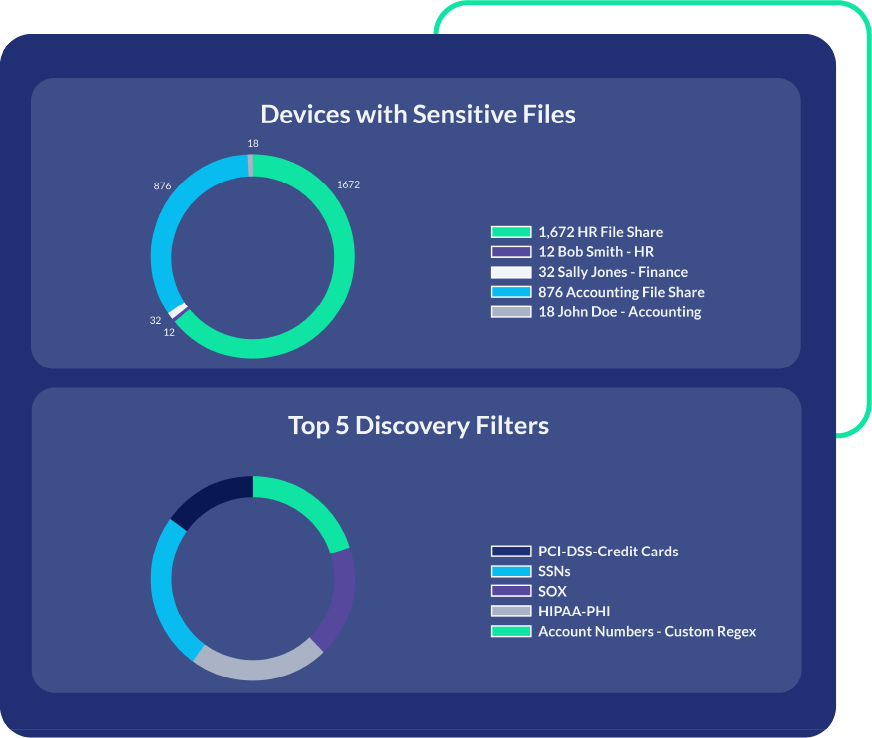
PK Protect uses contextual awareness and AI-driven computer vision to locate sensitive data with accuracy. It performs with precision and efficiency in the most demanding environments. One major U.S. bank uses the platform to scan over 400 applications and 18,000 databases containing nearly a million tables.








