
Trusted By Leading Organizations for Over 40 Years
Protect What IAM Can’t
IAM and Multi-Factor Authentication (MFA) solutions reduce risk by verifying users and applications, grouping them appropriately, and controlling access to sensitive information. While these measures are critical, they fall short of meeting modern data protection standards on their own.
PK Protect delivers security that integrates with and elevates your existing IAM & MFA tools. It encrypts data at rest and in motion and automatically de-identifies PII and PHI in structured and unstructured data sets.
Stop relying on “check the box” security and gain the confidence of end-to-end data security.
Don’t Settle for a Deadbolt, When You Can Have a Bank Vault
End-to-End Data Security

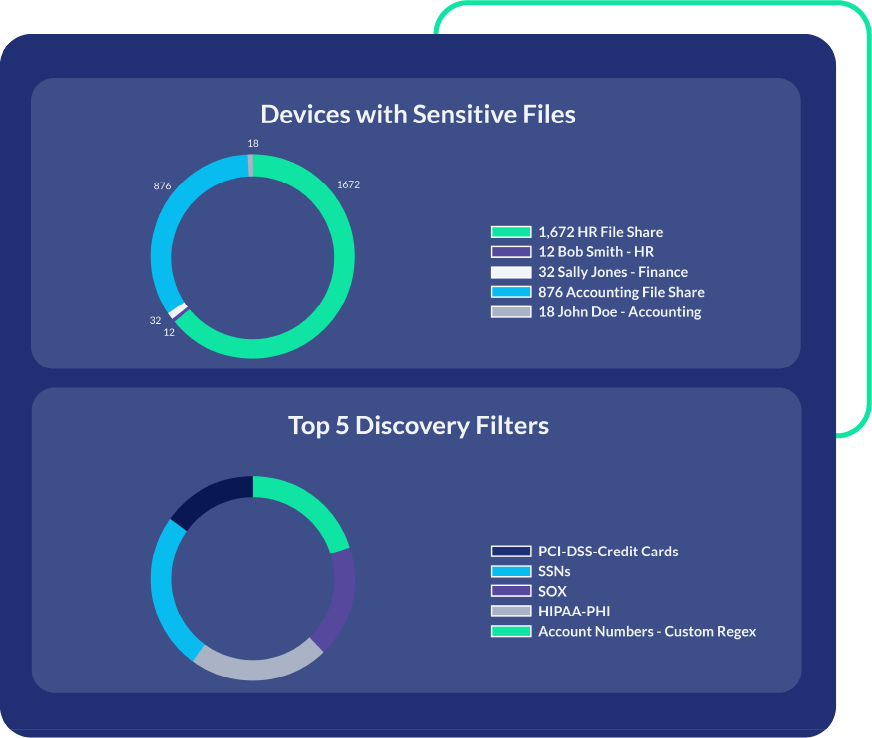
Granular Discovery
Before you can enforce access controls, you need full visibility into your data. Our data discovery pinpoints where sensitive and propriety information lives across your enterprise, giving you the clarity you need to take informed action to secure data.
Classify and Control your Data
Once sensitive data is identified, classification enables you to categorize and control it effectively. PK Protect enforces policies based on data content. This eliminates reliance on user decisions and avoids large, manual security projects.
With data properly classified, PK Protect can automatically route it to appropriate storage locations and deliver intelligence to IAM tools, enabling accurate enforcement of access and hierarchal controls.


Encryption is the Securest Form of IAM
While PKWARE offers multiple ways to enable safe data use, encryption works together with access management to protect sensitive information. Encryption prevents unauthorized access, accidental data loss, and overly permissive sharing. It stays with the data even after it leaves the organization.







