Continuous Protection and Compliance
Across Your Enterprise
Leveraged by 21 of the top 25 U.S. banks, PK Protect automatically
discovers and protects data at enterprise scale, without complexity.
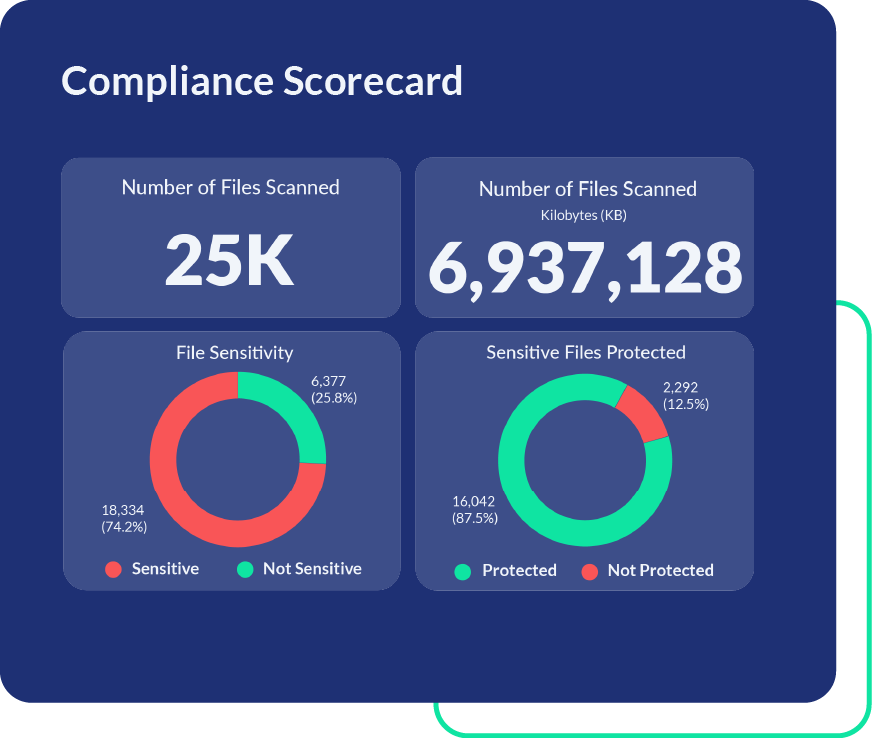
Ensure Compliance
Go beyond checking a box. Exceed complex regulatory requirements like PCI DSS, GLBA, SOX, GDPR, CCPA and HIPAA, pass audits with ease, and avoid costly fines. PK Protect simplifies compliance with a centralized platform for managing diverse enforcement and reporting needs across all repositories. This approach helps you demonstrate to auditors that sensitive data has been fully identified and protected.
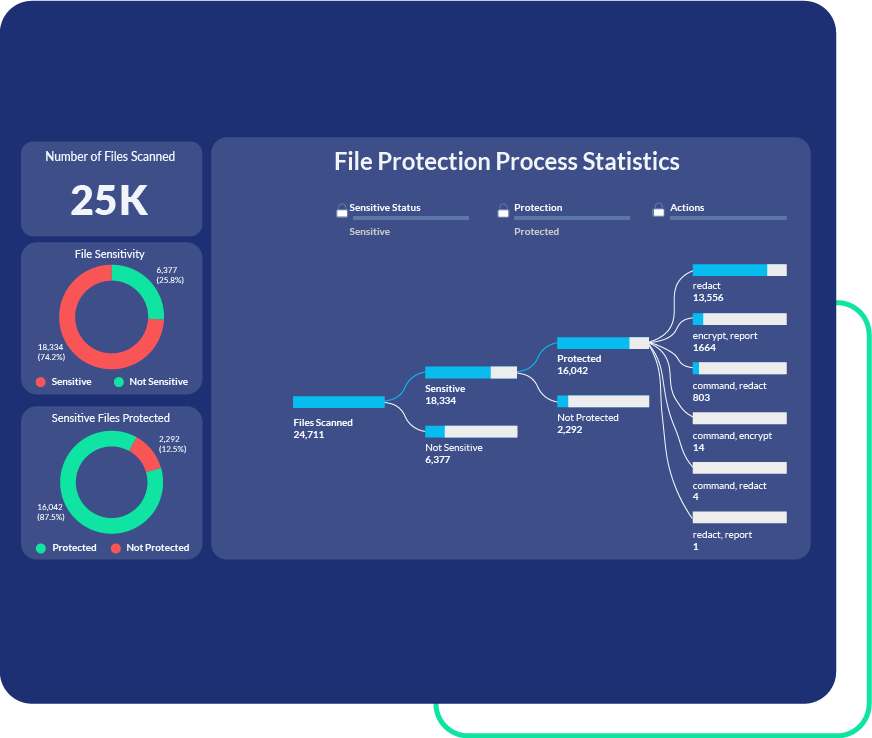
Strengthen Data Breach Resilience
Mitigate risk and exposure with security that stays with your data, at rest and in motion. Discover and protect your data before a breach occurs. PK Protect gives you full visibility into all data and ensures that in the event of a breach, sensitive data remains inaccessible to unauthorized users.
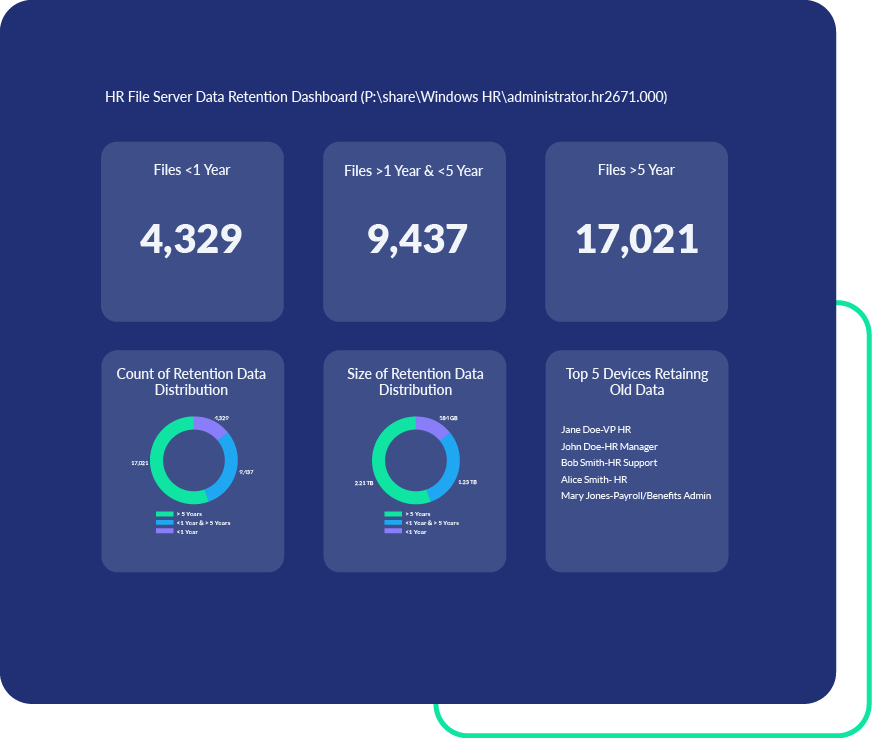
Optimize Data Retention
Reduce risk and storage costs by eliminating redundant, obsolete, and trivial (ROT) data. PK Protect automatically discovers outdated or unnecessary data across the enterprise and minimizes your attack surface by removing or remediating it with flexible, policy-driven protection options.
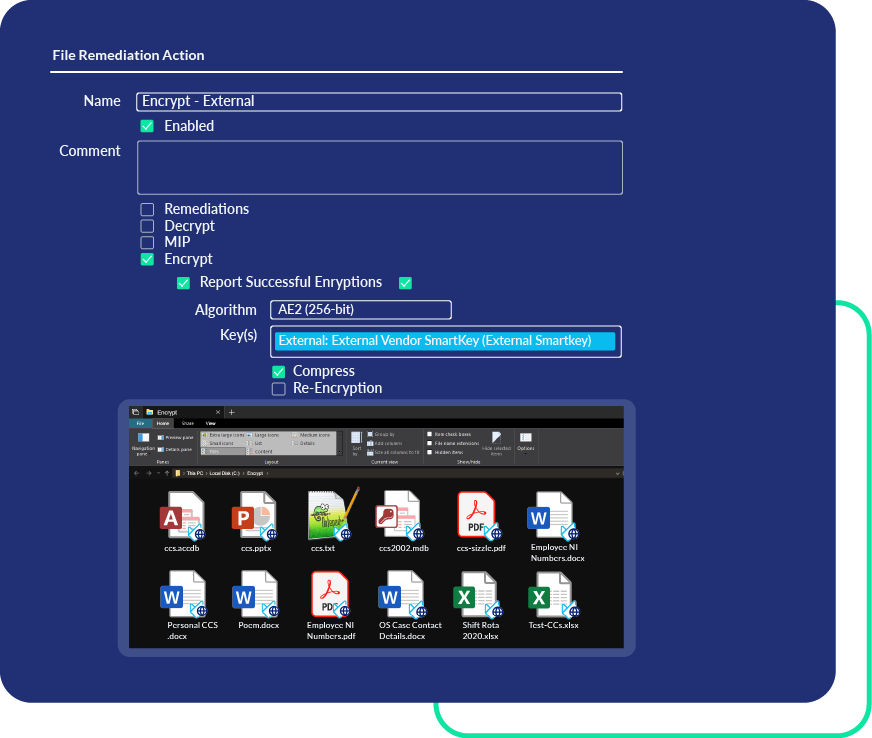
Use and Share Data Securely
Unlock your data’s value without incurring risk. Automated masking, redaction, and encryption secure data while keeping it usable and shareable. Encrypt files and servers to ensure secure access for authorized users. Masking de-identifies copies of production data so developers can safely use it in lower environments and obfuscates data before it enters AI models, preventing exposure while preserving utility.
Data Protection, Everywhere
The PK Protect Approach to Data Security









