Data Centric DSPM Security
PKWARE’s DSPM platform, PK Protect, uses advanced discovery to deliver complete visibility into sensitive data across your enterprise. It automatically remediates risk, embedding protection into the data itself. With security that travels with your data, sensitive information always remains secure.
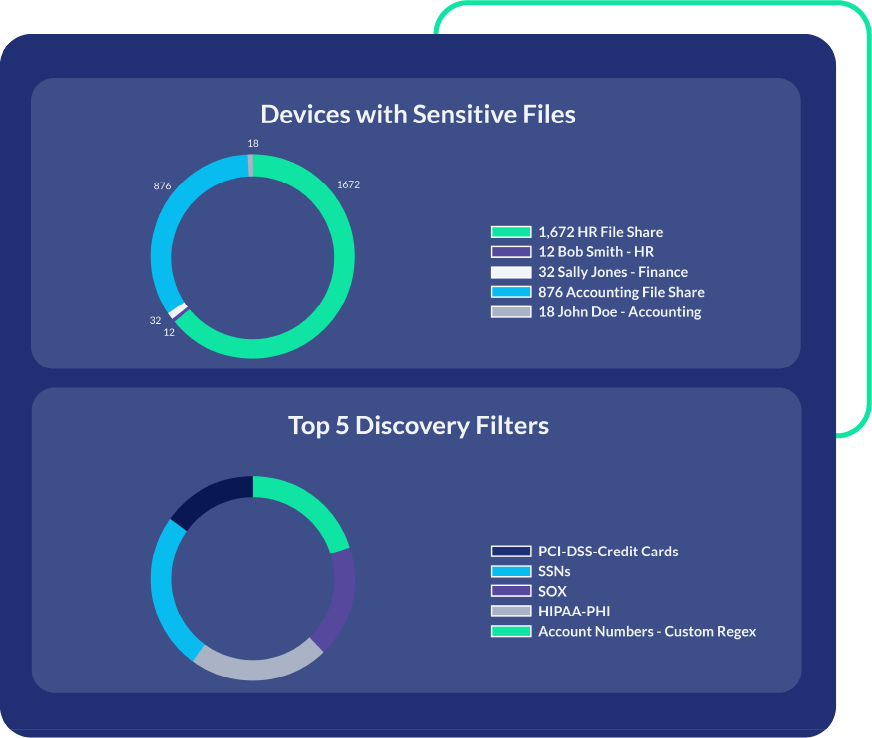
Simplified DSPM with Unified Discovery and Protection
DSPM Security Features
Our DSPM platform offers enhanced capabilities to fortify your data security posture.

Comprehensive, Accurate, and Scalable Data Discovery
Leverage precise discovery across your entire enterprise. Contextual awareness and AI-driven computer vision locate sensitive information with accuracy. PK Protect also scans efficiently, even in the most demanding environments. For example, one major U.S. bank uses our DSPM platform to scan over 400 applications and 18,000 databases containing nearly a million tables.
Automated Remediation
Automatically apply centralized protection policies for consistent data security across every environment. Choose to encrypt, redact, mask, move, delete, or quarantine sensitive data. These actions allow for proactive security and compliance. Protections integrate into existing workflows to ensure security without disrupting users or operations.


Microsoft Purview Integration
PK Protect integrates with Microsoft Purview to apply and enforce sensitivity labels automatically. It centralizes labeling based on content and extends protection through encryption and redaction available for file types that Microsoft labeling doesn’t support.