Navigating Compliance Regulations Doesn’t Have to Be Complicated
Adhering to regulations like PCI DSS, HIPAA, GDPR, CCPA, GLBA, and FISMA is demanding and complex, especially when data spans multiple environments. PK Protect makes it simple. With automated discovery and protection of sensitive data across your enterprise, you can stay ahead of requirements, pass audits, and avoid costly penalties.
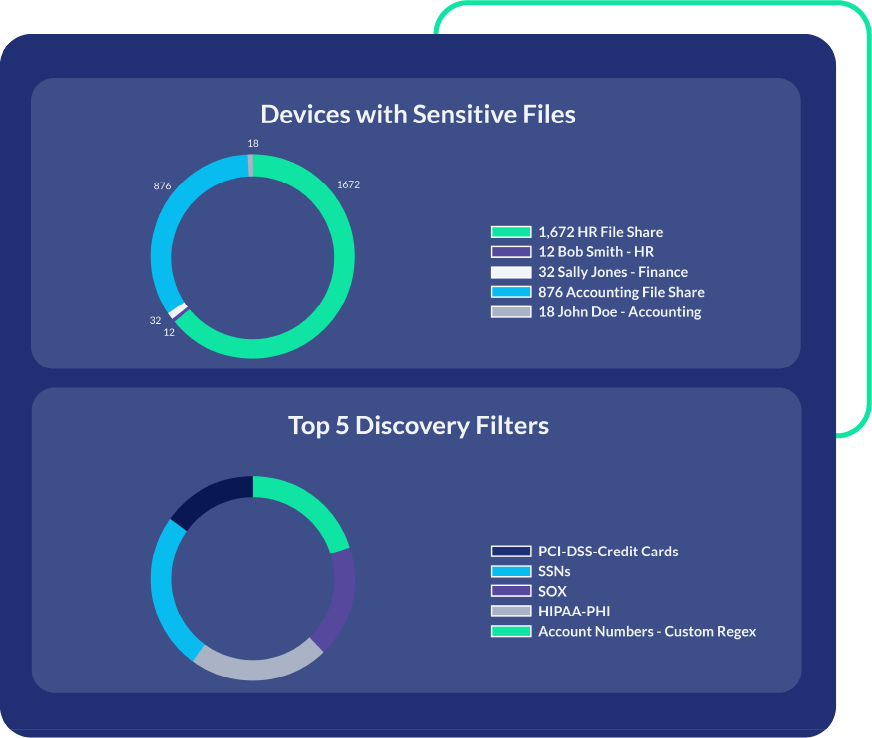
Overcome Regulatory Hurdles
Achieve and demonstrate data compliance with ease.
PK Protect Data Compliance Solutions

Policy-Based Remediation—At Rest and In Transit
Apply automated encryption, redaction, or masking to meet compliance standards. Regulations such as HIPAA, GLBA, PCI DSS, and FISMA require sensitive data to be encrypted both at rest and in transit. PK Protect delivers this without creating unnecessary friction for users.








