The Ripple Effect of A Data Breach
The after effects of a data breach can reach far and wide. Lesser seen impact can include the cost of remediation, revenue loss, reputational harm, national security, even human life. The ripple effect of indirect costs—monetary and otherwise—can end up impacting a company’s bottom line for years.
Accounting for the Resolution Process
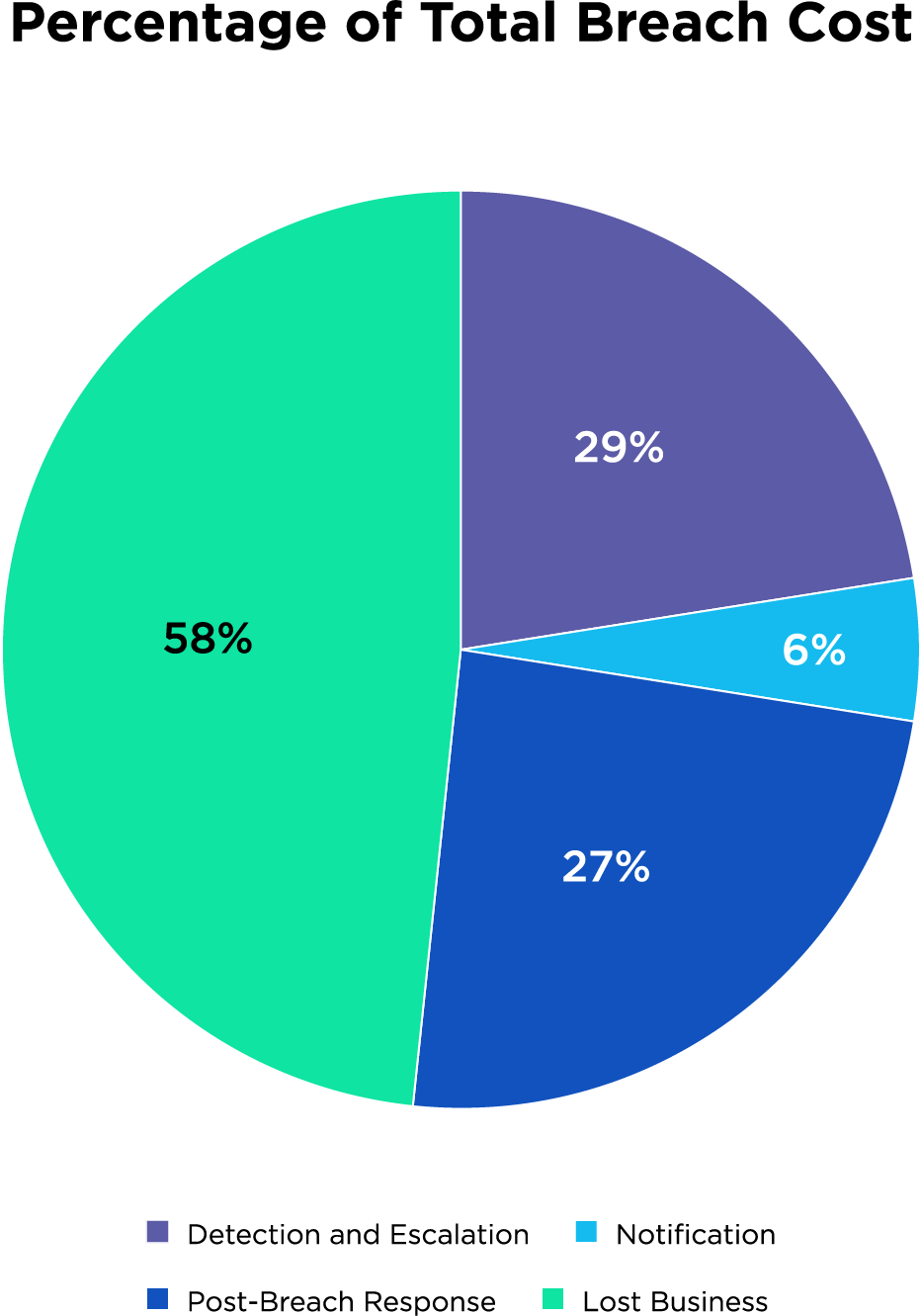
Breaking a data breach into accounting terms, companies can expect to segment the resolution process into four cost centers: Detection and Escalation, Notification, Post-Breach Response, and Lost Business.
- Detection and Escalation
This first cost center is most often involved in the initial “pebble drop” cost, encompassing all the activities that enable a company to reasonably detect the data breach, and amounting to approximately 29 percent of the total cost of the data breach. Based on the global average of $4.24 million, the price tag hovers at $1.24 million.
- Notification
Many data compliance regulations such as HIPAA, the EU’s General Data Protection Regulation (GDPR), and the California Consumer Privacy Act (CCPA) require that customers whose data has been impacted by a breach be notified within a set period of time. Failure to do so results in significant fines for the organization. Even without the line item of a notification fine, the activities that ultimately allow the company to notify those impacted as well as data protection regulators and other third parties accounts for six percent ($0.27 million) of the total cost of the breach. Any organization that does not notify their customers within the expected parameters can expect to see additional fines down the line.
- Post-Breach Response
It’s not enough to simply notify customers of a data breach. With brand reputation now at risk, it’s crucial to provide activities that will help the victims of the breach communicate with the company, and remedy the issues as much as possible with victims and regulators. These actions could include credit monitoring, product discounts, legal costs, even the cost of time needed to issue new accounts or cards. This cost center carries a larger percentage of the total average monetary cost of a breach at 27 percent, or $1.14 million.
Regulatory fines for data breaches also typically fall into the Post-Breach Response cost center. These are the top factors for amplifying the data breach costs. To compound the issue, these costs aren’t necessarily incurred at the time the breach is discovered or remedied—20 percent of costs in highly regulated industries are incurred as far out as two years after the breach.
- Lost Business
The largest share of the average cost at 38 percent ($1.59 million), this cost center accounts for all activities enacted to minimize customer attrition, disruption of business, and revenue loss. This includes replacing revenue lost during system downtime, as well as detractors such as reputation loss. Not only will established customers leave—breached organizations may lose up to a third of their existing customer base—media and word of mouth may make it difficult to attract new customers depending on the depth and severity of the data breach. Data security notwithstanding, it is already estimated to cost five times as much to attract a new customer than to keep an existing one. A publicized breach could increase that price tag significantly.
These four cost centers represent distinct areas with measurable dollar amounts tied to them, costs that reveal layer after layer as teams work to control and resolve a data breach. But beyond the dollar amounts, companies must also consider the cost of time as they work to return to “normal.”
Time is Money
Naturally, the longer a breach goes on, the more impact it has on the business. According to one McAfee survey of 500 senior IT decision makers, they believed it took an average of only 10 hours to detect a data breach. Studies and anecdotal evidence suggest otherwise. The Verizon Data Breach Investigation Report found that 66 percent of breaches weren’t found for months or even years.
According to IBM, it takes on average 287 days to identify and contain a data breach, the breakdown of which averages 212 days to identify and 75 days to contain the breach. This means that if a breach occurred on January 1, it would not be fully contained until October 14. The post-COVID shift to more remote and hybrid work only exacerbates this issue: Organizations that have a workforce made of more than 50% remote employees averaged a full 306 days to contain the breach—235 days to identify, and 81 to contain. If their breach began on January 1, it would span all the way through November 12 before being fully contained.
Reducing Risk and Cost with PKWARE
The impact of a data breach is felt far beyond just the theft of or inability to access sensitive and private data. The ability of a business to do what a business does—produce and sell their products and services under a trusted brand—also hangs in the balance, and each ripple felt after a data breach comes with a price tag.
Find out how you can reduce the cost of a data breach at your organization with preemptive data discovery and remediation from PKWARE. This free demo shows you how.
Want to learn more? Check out our accompanying infographic, The Ripple Effect of A Data Breach.

The after effects of a data breach can reach far and wide. Lesser seen impact can include the cost of remediation, revenue loss, reputational harm, national security, even human life. The ripple effect of indirect costs—monetary and otherwise—can end up impacting a company’s bottom line for years.
Accounting for the Resolution Process
Breaking a data breach into accounting terms, companies can expect to segment the resolution process into four cost centers: Detection and Escalation, Notification, Post-Breach Response, and Lost Business.

- Detection and Escalation
This first cost center is most often involved in the initial “pebble drop” cost, encompassing all the activities that enable a company to reasonably detect the data breach, and amounting to approximately 29 percent of the total cost of the data breach. Based on the global average of $4.24 million, the price tag hovers at $1.24 million.
- Notification
Many data compliance regulations such as HIPAA, the EU’s General Data Protection Regulation (GDPR), and the California Consumer Privacy Act (CCPA) require that customers whose data has been impacted by a breach be notified within a set period of time. Failure to do so results in significant fines for the organization. Even without the line item of a notification fine, the activities that ultimately allow the company to notify those impacted as well as data protection regulators and other third parties accounts for six percent ($0.27 million) of the total cost of the breach. Any organization that does not notify their customers within the expected parameters can expect to see additional fines down the line.
- Post-Breach Response
It’s not enough to simply notify customers of a data breach. With brand reputation now at risk, it’s crucial to provide activities that will help the victims of the breach communicate with the company, and remedy the issues as much as possible with victims and regulators. These actions could include credit monitoring, product discounts, legal costs, even the cost of time needed to issue new accounts or cards. This cost center carries a larger percentage of the total average monetary cost of a breach at 27 percent, or $1.14 million.
Regulatory fines for data breaches also typically fall into the Post-Breach Response cost center. These are the top factors for amplifying the data breach costs. To compound the issue, these costs aren’t necessarily incurred at the time the breach is discovered or remedied—20 percent of costs in highly regulated industries are incurred as far out as two years after the breach.
- Lost Business
The largest share of the average cost at 38 percent ($1.59 million), this cost center accounts for all activities enacted to minimize customer attrition, disruption of business, and revenue loss. This includes replacing revenue lost during system downtime, as well as detractors such as reputation loss. Not only will established customers leave—breached organizations may lose up to a third of their existing customer base—media and word of mouth may make it difficult to attract new customers depending on the depth and severity of the data breach. Data security notwithstanding, it is already estimated to cost five times as much to attract a new customer than to keep an existing one. A publicized breach could increase that price tag significantly.
These four cost centers represent distinct areas with measurable dollar amounts tied to them, costs that reveal layer after layer as teams work to control and resolve a data breach. But beyond the dollar amounts, companies must also consider the cost of time as they work to return to “normal.”
Time is Money
Naturally, the longer a breach goes on, the more impact it has on the business. According to one McAfee survey of 500 senior IT decision makers, they believed it took an average of only 10 hours to detect a data breach. Studies and anecdotal evidence suggest otherwise. The Verizon Data Breach Investigation Report found that 66 percent of breaches weren’t found for months or even years.
According to IBM, it takes on average 287 days to identify and contain a data breach, the breakdown of which averages 212 days to identify and 75 days to contain the breach. This means that if a breach occurred on January 1, it would not be fully contained until October 14. The post-COVID shift to more remote and hybrid work only exacerbates this issue: Organizations that have a workforce made of more than 50% remote employees averaged a full 306 days to contain the breach—235 days to identify, and 81 to contain. If their breach began on January 1, it would span all the way through November 12 before being fully contained.
Reducing Risk and Cost with PKWARE
The impact of a data breach is felt far beyond just the theft of or inability to access sensitive and private data. The ability of a business to do what a business does—produce and sell their products and services under a trusted brand—also hangs in the balance, and each ripple felt after a data breach comes with a price tag.
Find out how you can reduce the cost of a data breach at your organization with preemptive data discovery and remediation from PKWARE. This free demo shows you how.
Want to learn more? Check out our accompanying infographic, The Ripple Effect of A Data Breach.


