DSAR Fulfillment Made Simple
Keeping up with DSARs is cumbersome and creates unnecessary operational strain. PK Protect streamlines DSAR fulfillment, ensures regulatory compliance, and minimizes errors by automating data discovery with speed and accuracy.
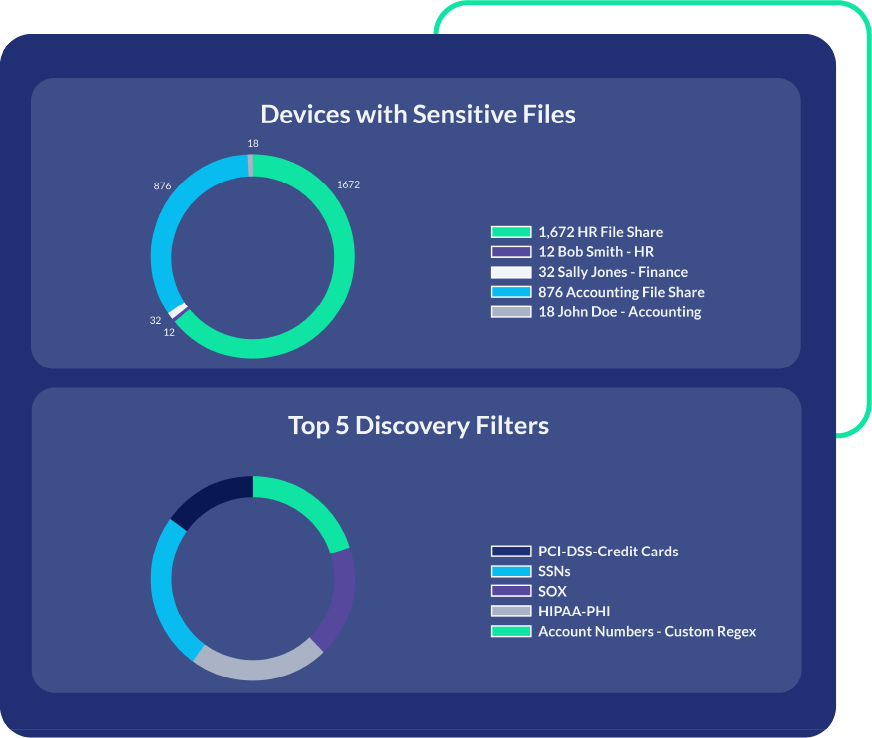
Transform DSAR Chaos into Seamless Compliance
Stop scrambling to meet DSAR deadlines. Automate the process and demonstrate compliance with PK Protect discovery.
Data Privacy Features

Discovery to Remove Customer Data
Scan across repositories to find customer data so you can delete it based on DSARs.
Reporting to Support DSAR
Generate a report that details everywhere the subject’s data resides in your infrastructure to assist with DSAR fulfillment.









