Transform Sensitive Data for Safe Use
Your organization’s data has immense value. But how can you leverage that value without introducing risk? PK Protect solves this with data masking. Masking replaces sensitive alphanumeric characters with different random characters in the same format, effectively rendering the data non-sensitive. Prevent exposure while keeping data functional for critical business needs.
Masking for Secure, Compliant Data Use
Advantages of PK Protect Data Masking

Enterprise-Wide Data Masking
Our data masking solution secures sensitive data across hundreds of platforms, including Oracle, SQL Server, Postgres, DB2, Hadoop, AWS, Azure, Snowflake, Salesforce, and more. Ensure security and compliance for your entire data landscape.
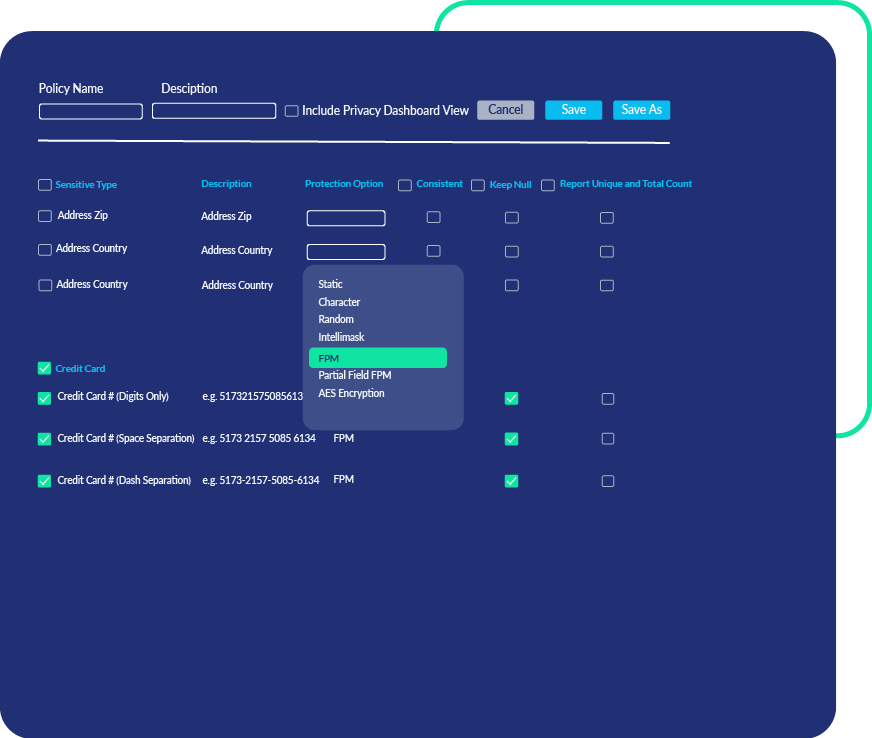
Centralized Policies
PK Protect masks sensitive data via policies that incorporate both discovery and masking across all repositories in your environment. This prevents gaps in your data security strategy.


Referential Integrity
Our platform maintains referential integrity by masking individual data elements consistently across the various platforms in which they reside. This provides a more realistic representation of production datasets for accurate and meaningful development and analytics.






