
Trusted By Leading Organizations for Over 40 Years
Go Beyond Perimeter Defense and Access Control
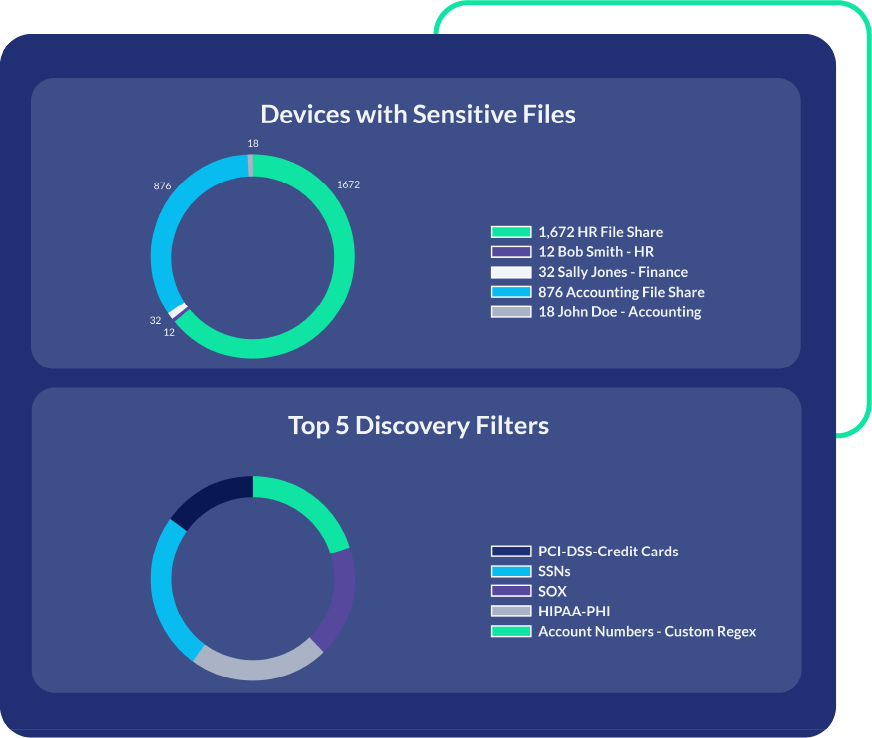
PK Protect delivers an integrated platform for sensitive data discovery and protection. Our solution enables organizations to ensure compliance, limit exposure risk, enforce retention policies, and use and share data securely. Unlike traditional DLP and access control, PK Protect embeds security into the data—at rest or in motion. This provides persistent protection across the enterprise. Safeguard data at the asset level for true end-to-end security that legacy approaches can’t match.
Secure Every Environment With One Platform
Eliminate silos and simplify your security strategy.
How Data-Centric Security Benefits Your Organization











